Working with Yandex Cloud from inside a VM
This section describes how to work with Yandex Cloud from inside a VM via the API or CLI.
To automate operations with Yandex Cloud from inside a VM, we recommend using service accounts. This is more secure since you do not need to save your OAuth token on a VM and can restrict access rights to a service account.
Yandex Cloud provides simplified authentication via the API and CLI from inside a VM for service accounts. To authenticate:
- If you do not have a service account yet, create one and configure access rights for it.
- Link the service account to your VM.
- Authenticate from inside a VM.
Link your service account
Link your service account to an existing or new VM. You can only link one service account.
To link a service account to a VM, you must have permission to use this account. This permission is included in the iam.serviceAccounts.user and editor roles and higher.
Linking to an existing VM
- In the management console
- Select Compute Cloud.
- Click the VM name.
- Click
- Under Access, select an existing service account or create a new one.
- Click Save changes.
If you do not have the Yandex Cloud command line interface yet, install and initialize it.
The folder specified in the CLI profile is used by default. You can specify a different folder using the --folder-name or --folder-id parameter.
Update the VM parameters by specifying the service account via the --service-account-name or --service-account-id option:
yc compute instance update my-instance --service-account-name test
Use the update REST API method for the Instance resource or the InstanceService/Update gRPC API call. Specify the service account ID in your request.
Linking to a new VM
In the management console, you can link a service account that is in the same folder as the new VM. If the service account is in a different folder, use the CLI or API.
To link your service account to a VM, specify it when creating the VM. You can select an existing service account or create a new one:
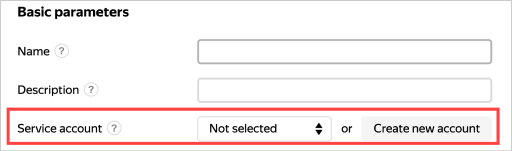
If you do not have the Yandex Cloud command line interface yet, install and initialize it.
The folder specified in the CLI profile is used by default. You can specify a different folder using the --folder-name or --folder-id parameter.
Create a VM and specify the service account using the --service-account-name or --service-account-id option:
yc compute instance create \
--name my-instance \
--network-interface subnet-name=default,nat-ip-version=ipv4 \
--ssh-key ~/.ssh/id_ed25519.pub \
--service-account-name my-robot
Use the create REST API method for the Instance resource or the InstanceService/Create gRPC API call. Specify the service account ID in your request.
Authenticating from inside a VM
To authenticate from inside a VM on behalf of the linked service account:
-
Connect to your VM over SSH.
-
If you do not have the Yandex Cloud command line interface yet, install and initialize it.
-
Create a new profile:
yc config profile create my-robot-profile -
Configure your profile to run commands.
Some commands require that you specify unique IDs for your cloud and folder. You can specify their details in the profile or use a specific flag for these commands.
-
Specify the cloud in your profile:
yc config set cloud-id <cloud_ID>Or run commands with the
--cloud-idparameter. -
Specify a folder in the profile:
yc config set folder-id <folder_ID>Or run commands with the
--folder-idparameter.
All operations in this profile will be performed on behalf of the linked service account. You can change the profile parameters or switch to another profile.
You can also get a Yandex Identity and Access Management token, for example, to authenticate with the API:
yc iam create-tokenThe lifetime of an Identity and Access Management token in this case will be less than 12 hours. Request an Identity and Access Management token more often, e.g., every hour. To learn the remaining token lifetime, use the API instructions.
-
-
Connect to the VM via SSH.
-
Get an Identity and Access Management token from metadata in Google Compute Engine format:
curl -H Metadata-Flavor:Google http://169.254.169.254/computeMetadata/v1/instance/service-accounts/default/token {"access_token":"CggVAgAAA...","expires_in":39944,"token_type":"Bearer"}The Identity and Access Management token will be returned in the
access_tokenfield of the response. The remaining lifetime of the Identity and Access Management token is specified in theexpires_infield. -
Specify the received IAM token when accessing Yandex Cloud resources via the API. Pass the IAM token in the
Authorizationheader in the following format:Authorization: Bearer <IAM token>
Keep track of the Identity and Access Management token lifetime or request a new token more often, e.g., every hour.