How access management works in Yandex Cloud
Here you can learn how to manage access to your resources and how IAM checks access rights for the resources.
How are access rights verified?
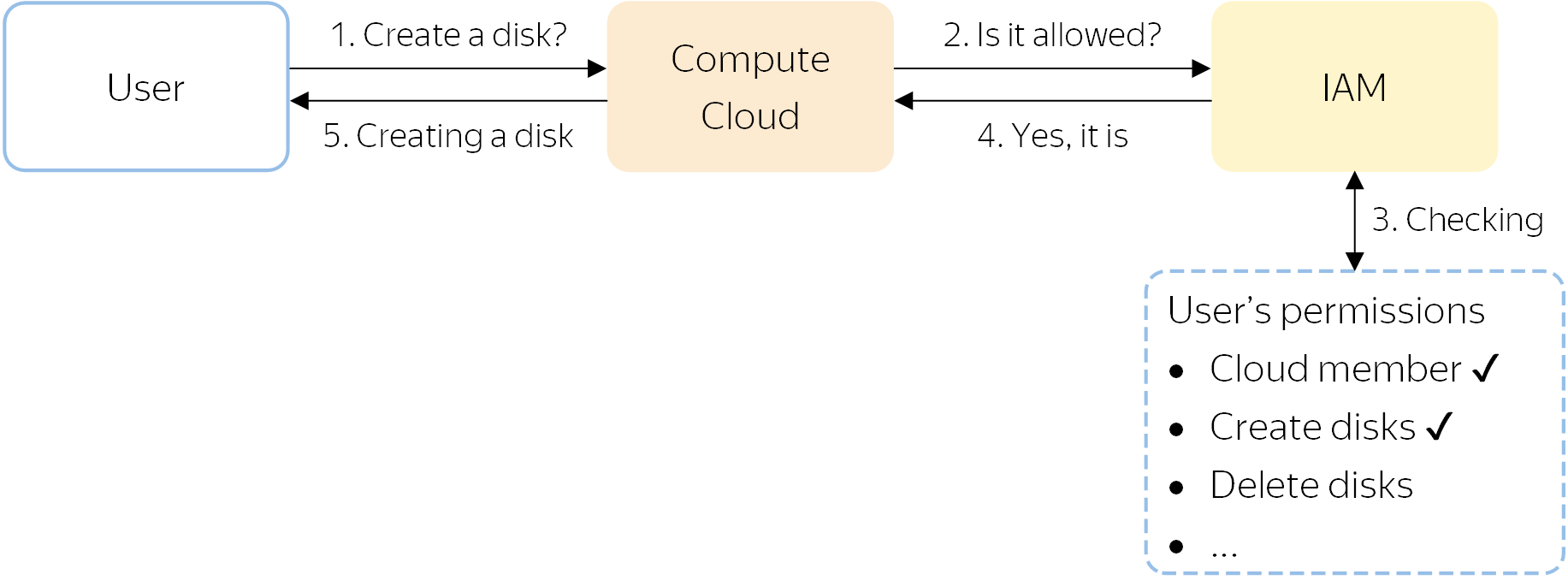
All operations in Yandex Cloud are first sent for verification to IAM. For example:
- A user requests Compute Cloud to create a new disk in the
default
folder. - The service sends a request to IAM to check whether this user is allowed to create disks in this folder.
- IAM checks if the user is a member of the cloud with the
default
folder and has the necessary permissions to create a disk in this folder. - If any of the permissions are missing, the operation is not allowed and Yandex Cloud returns an error.
If all the required permissions were granted, IAM reports this to the service. - The service creates a new disk.
How do I perform access management?
Access management in Yandex Cloud leverages the Role Based Access Control
To assign a role, select a resource, choose a role, and describe the subject assigned the role. This allows you to bind access rights to the resource.
You can also assign a role to a parent resource that access rights are inherited from, such as a folder or cloud.
Warning
It usually takes 5 seconds or less to update access rights. If the role was assigned to you, but you do not have access yet, repeat the operation.
For example, you were given the right to create folders in the cloud and you were able to create one folder, but couldn't create another one. This is because the access rights have not yet been updated on the server where the second create folder operation was performed. Try creating the folder again.
Resources that roles can be assigned for
You can assign roles for a cloud, folder, and other resources from the list. If you need to grant access to a resource that is not on the list, e.g., a Yandex Managed Service for PostgreSQL cluster, assign the role to the parent resource it inherits permissions from. Managed Service for PostgreSQL clusters inherit access permissions from their folder.
Role
Resource roles can be assigned by users with the administrator role for the resource, as well as the owners of the cloud that the resource belongs to.
Each role consists of a set of permissions that describe operations that can be performed with the resource. A user can assign a role with only those permissions which are available to themselves. For example, only the user with the cloud owner role can assign this same role. The administrator role is not enough for this.
To find out what roles exist and what permissions they include, see Roles.
Subjects that roles are assigned to
Roles are assigned to subjects. The following subject types are available:
-
userAccount: Yandex account added to Yandex Cloud. -
serviceAccount: Service account created in Yandex Cloud.You can assign roles to a service account for any resources in any cloud if these resources belong to the same organization as the service account. You can also assign roles to a service account for the organization.
-
federatedUser: User account in an identity federation, e.g., Active Directory. -
group: User group created in Yandex Cloud Organization. -
system: System group.
Access binding
Roles to a resource are assigned as a list of role-subject bindings. They are called access bindings. You can add or remove these bindings to control access rights to a resource.
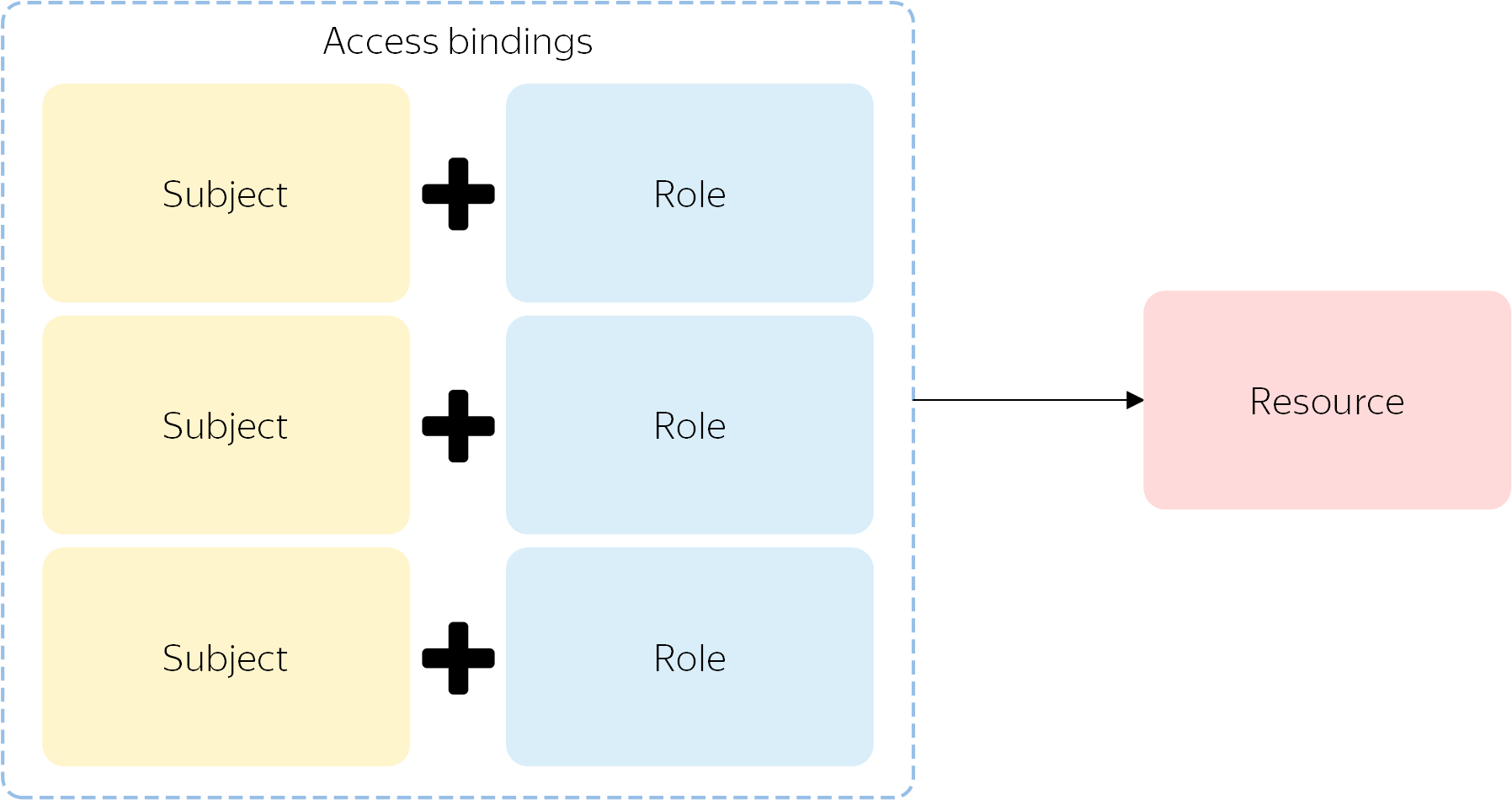
Each binding is a single assignment of a role to a subject. To assign a user multiple roles to a resource, set a separate binding for each role.
Inheritance of access rights
If a resource has child resources, all permissions from the parent resource will be inherited by the child resources. For example, if you assign a user a role for a folder where a VM instance resides, all permissions of this role will also apply to the instance.
If a child resource is also assigned some roles, a list of permissions for this resource will be combined with a list of permissions for its parent resource. You cannot limit the list of permissions inherited from the parent resource.
Impersonation
Impersonation occurs when a user performs certain actions with cloud resources on behalf of a service account with the appropriate permissions. Impersonation is mostly used to temporarily expand user permissions without generating static credentials for the user.
For example, the user needs temporary permissions for viewing a folder they do not have view access for. The administrator can assign a role for viewing the folder to the service account, and assign the special iam.serviceAccounts.tokenCreator role to the user. As a result, the user can view the folder's resources on behalf of the service account or obtain an IAM token for the service account. The user cannot edit permissions or delete the service account.
The administrator can revoke the role whenever needed.
Access control restrictions in the management console
Some restrictions apply to assigning roles in the management console:
- You cannot assign roles to multiple subjects at once, unlike in the API or CLI. In the management console, you should first select the subject (user or service account) and then assign roles to it.
See also
For more information about managing access to a specific Yandex Cloud service, see the Access management
section in the documentation for that service.
Step-by-step guides and examples: